Digital asset security and protection
- Jul 20, 2023
- 7 min read

For any asset owner the security and protection of their assets is always the basic duty of the custodians they appoint. It is akin to a form of insurance. In this respect, cryptocurrencies and digital assets do not differ from conventional assets.
However, the history of hacks and thefts in the cryptocurrency and DeFi industries means that this fundamental duty is of particular concern. Criminals have provided remarkably adept at stealing cryptocurrencies, switching from hacking exchanges (where many of the thefts were inside jobs) to exploiting weaknesses in inter-protocol “bridges,” smart contracts and DeFi applications.
Fortunately, independent third-party custody of cryptocurrency has proved remarkably safe, with no customer assets being lost by independent custodians until the failure of Prime Trust in June 2023. All of the respondents to the 2023 Future of Finance survey of digital asset custodians that answered the question affirmed that they had never lost customer assets.
This record is surprising, given the lower barriers to entry to the digital asset custody market. Normal criteria such as capital, regulatory licences, independent audit and internal control structures were secondary to the technological capability to provide a service at all.
That service has had to adapt rapidly to the changing patterns of cryptocurrency trading activity. The development of “prime brokerage” services, for example, followed pressure on digital asset custodians to sponsor client buy and sell orders on multiple exchanges out of a single custody account.
But, the assets being digital, technology is central to digital asset custody services because it is the main point of vulnerability.
Digital asset custody technology is trapped in a Red Queen race to stay ahead of equally sophisticated hackers, many of them State-sponsored. Already, some digital asset custodians are claiming to offer protection from hackers armed with quantum computers that can break present, prime number-based cryptographic encryption.
The principal purpose of digital asset custody technology is to ensure the safety of private keys. This is because cryptocurrencies are “bearer” instruments. As the cryptocurrency industry aphorism has it, “not your keys, not your coins” (the same is not true of other digital assets, such as security tokens, where stolen assets can be destroyed and replaced by a registration function).
So far, the cryptocurrency industry has developed three main technological techniques for protecting private keys.
The first is Hardware Security Modules (HSM). As the name suggests HSM describes a physical computing device – though there are now Cloud-based HSMs - that safeguards and manages digital keys, performs encryption and decryption functions for digital signatures, and offers strong transaction authentication and other cryptographic functions.
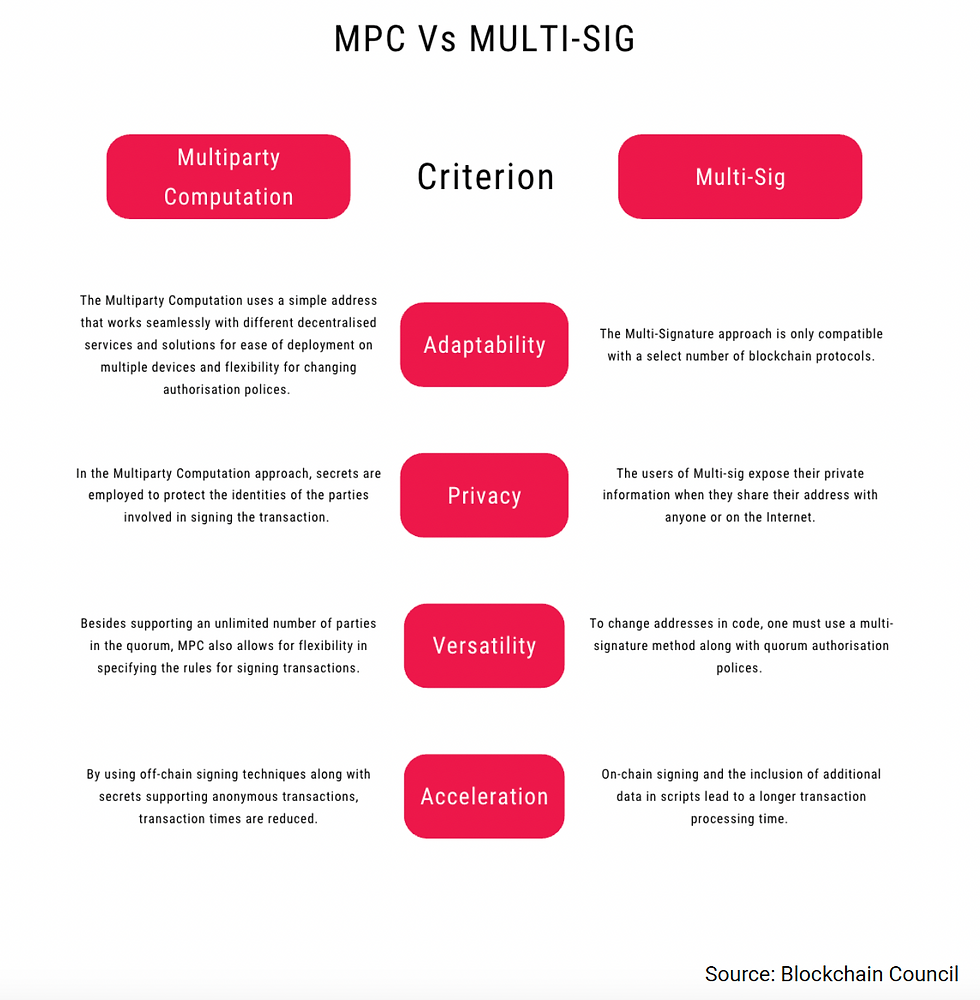
The main risk HSM struggles to mitigate without additional measures is that control of the keys can be acquired by a single person who works for the custodian (or a hacker). It was to solve this problem that two other techniques were developed. The first is Multi-signature Wallets (Multisig). The other is Multi-party Compution (MPC)
Multisig imposes, at its simplest, the requirement for more than one signatory to authorise a transaction. It is the on-chain equivalent of multiple actors with their own private keys coming together to sign a transaction. Usually, the client as the ultimate owner of the asset - or the asset manager to which the asset owner has delegated control of the portfolio - initiates the transaction, which must be co-signed by the custodian.
Multisig has proved hard to scale as transaction volumes increase. The fact that multiple private keys are stored in different places is also not proof against their being compromised by hackers or fraudsters.
MPC solves the single point of failure by replacing indivisible private keys by giving multiple participants a piece of data about a key that enables the participants collectively to compute the key while keeping their own piece of data secret. The separation of pieces of the key makes it much harder for malicious actors to locate all the pieces to unlock the asset. MPC needs more computational resources to run, so tends to be slower.
But neither Multisig nor MPC is the final destination of private key protection. New services are being developed whose proponents claim they offer superior security, flexibility and ability to integrate with any blockchain protocol.
The second layer of protection for digital assets that the cryptocurrency industry has developed is internal procedural policies and controls. These lay down the processes employees of digital asset custodians must follow. They also set controls designed to pick up breaches of compliance and to limit attacks on software.
The policies and controls are similar to those used by regulated custodian banks to align their business with a typical technology risk management framework.
Box 1
Customer Asset Security Policies, Procedures and Controls Digital Asset Custodians Should Follow The key policies, procedures and controls digital asset custodians must implement are:
Source: NIST |
Increasingly, digital asset custodians must provide clients with a second layer of assurance: external standards that attest to the efficacy of their internal policies, procedures and controls.
The basic form of external validation is to publish financial records audited by a recognised and reputable accounting firm. The case of FTX is reminder that this essential requirement was not always met in the cryptocurrency industry.
More granular sources of external validation favoured by digital asset custodians include the System and Organisation Controls (SOCs) defined by The American Institute of Certified Public Accountants (AICPA).
There are three SOCs. SOC 1 provides the management of the digital asset custodian and its auditors with an independent opinion of the quality of the internal controls over financial information and reporting. This is germane to digital asset custody, since the existence of the assets and the authenticity of transactions and entitlements are governed entirely by the availability of information in digital form only.
The SOC 2 provides digital asset custodians’ management, customers and regulators with assurance that system controls are adequate to protect the security of assets, the availability of services, the ability to process transactions, and the confidentiality or privacy of information. The ability to deliver these benefits is crucial to the provision of a safe digital asset custody service.
The third SOC is used for potential customers that want an external review of the controls at a digital asset custodian they are using or propose to use, and so effectively repeats the work of a SOC 2 assessment but on behalf of a third party. A summary of SOCs 1 and 2 can be found in Table 1.
Table 1

Another external validation favoured by digital asset custodians is the International Standard on Assurance Engagements (ISAE) 3000 standard. Issued by the International Federation of Accountants (IFAC), the standard governs reports by accountants on the internal controls of a client. The report describes the controls and their objectives and assesses them against an industry norm.
Digital asset custodians have sought an ISAE 3402 certificate in particular because this assures clients that the firm meets SOC 1 requirements and has procedures in place to ensure it continues to do so.
Two out of three respondents to the 2023 Future of Finance survey of digital asset custodians have a SOC or ISAE certification or both; two out of five had a certificate of compliance with the ISO 27001 standard – the International Organisation for Standardisation (ISO) standard for information security management systems.
The third and final layer of assurance for clients: an insurance policy that makes customers whole if their assets are lost. Just shy of four out of five respondents to the 2023 Future of Finance survey of digital asset custodians have bought insurance.
The purpose of insurance, especially for digital asset custodians with limited capital, is obvious: it is to provide customers with assurance that, if something does go wrong, their assets will enjoy some level of financial protection.
That level of assurance varies. As digital assets are a new area of coverage for insurers, no standards have yet emerged over which risks are insurable or in what amounts. The policy purchased by the digital asset custodian might not cover all the assets or activities of a client, or provide sufficient cover for potential losses, especially if they are incurred in more than one incident.
This is why some investors have opted to purchase insurance directly. This eliminates reliance on the cover secured by the digital asset custodian, reducing the risk of conflict over who is covered for what risks in the event of a claim.
Some digital asset custodians boast that the level of security they provide means that clients should self-insure. However, institutional investors are likely to prefer the proxy insurance cover they have long purchased from traditional global custodians: the large balance sheet and borrowing capacity of a regulated bank.
